Cyber criminals are increasingly utilizing online advertisements for malicious purposes, often targeting individuals through regular Google searches.
These fraudulent activities, known as malvertising, are occurring more frequently with greater sophistication. In the autumn of 2023, Malwarebytes, a cybersecurity software firm, reported a 42% month-over-month increase in malvertising incidents in the United States.
According to Jérôme Segura, senior director of research at Malwarebytes, various brands are being targeted for phishing or malware distribution. He expressed that the current situation is merely the tip of the iceberg.
Rogue ads often appear as sponsored content during searches on both desktop and mobile devices. Additionally, malicious code can be concealed within ads on popular websites that consumers frequently visit.
While some of these ads only pose a threat to those who click on them, others can passively endanger individuals, simply by visiting an infected website, as stated by Erich Kron, security awareness advocate for KnowBe4, a security awareness and training company.
Segura also mentioned that corporate employees are potential targets of malvertising, citing examples involving major companies. For instance, Lowe’s staff members were targeted through a Google ad for an employee portal that claimed to be affiliated with the retailer.
By clicking on the link “myloveslife.net,” which misspelled the company’s name, users were directed to a phishing page featuring Lowe’s logo. This had the potential to mislead employees, given that many are unfamiliar with the URL for their internal website. ” You see the brand, even the official logo of that brand, and for you it’s enough to think it’s real,” Segura explained.
Another example involved an ad impersonating Slack, a communication tool owned by Salesforce. Initially, clicking on the ad redirected users to a pricing page on Slack’s official website. However, Segura discovered an impersonation scheme designed to deceive unsuspecting users into downloading something claiming to be the Slack app.
The issue of malvertising is not new, but cybercriminals are more sophisticated, creating ads that closely resemble legitimate ones, making it easy to be deceived. This problem is compounded by the widespread use and trust in search engines, particularly Google, where many of These Malicious ads are found.
“You see something appearing on a Google search, you kind of assume it is something valid,” explained Stuart Madnick, professor of information technology at MIT Sloan School of Management.
Consumers can also fall victim to malicious ads on trusted websites they regularly visit. While many of these ads are legitimate, some fraudulent ones can slip through the cracks. “It’s like the post office. Does the mailman check every letter you get to make sure it’s really from Publishers Clearing House?” Madnick analogized.
Consumers can take precautions to protect themselves from malvertising attempts. For example, they should refrain from clicking on sponsored links that appear during internet searches. The non-sponsored links, often located below the sponsored ones, are generally safer from malicious code or phishing attempts .
In the event of clicking on a sponsored link, it is advisable to check the URL at the top of the web page to ensure it matches the intended destination before proceeding further. For instance, when attempting to visit Gap.com, it is important to verify that the website is not Gaps.com.
Avinash Collis, assistant professor at Carnegie Mellon University’s Heinz College, advises consumers to promptly close the window if they find themselves on a suspicious site, as this action will likely prevent further issues.
Consumers should also exercise caution when encountering ads on trusted websites, according to Kron. For instance, if they come across advertisements for products priced significantly lower than elsewhere, Kron recommends refraining from clicking and instead visiting the official website of the product seller.
Most of the time, consumers can find special deals by searching on the provider’s site, or the deal will be prominently featured on the trusted website’s homepage.
Avoid contacting a phone number listed in a sponsored ad because it might be a fraudulent number. If you call it, hackers could gain access to your computer or personal information, depending on the scam, according to Chris Pierson, CEO of BlackCloak, a cybersecurity and privacy platform that offers digital executive protection for corporate executives.
Consumers should ensure that they are dialing a number from official product documentation they possess, Pierson advised. Alternatively, they could visit the company’s website for this information.
“Conducting a [web] search might yield results that are not endorsed by the company and phone numbers linked to cybercriminals.
All it takes to place an ad is money and, of course, cybercriminals who are stealing money have the means to pay for that bait,” Pierson explained.
Avoid ‘drive-by-downloads’
Consumers should also confirm that their computer and mobile phone operating systems and internet browsers are up-to-date.
So-called drive-by-downloads, which can affect individuals who simply visit a website infected with malicious codes, generally exploit a vulnerability in the user’s browser. This is less of a threat for individuals who keep their browsers and browser extensions up-to -date, according to Kron.
Consumers could also consider installing anti-malware software on their computer and phone. Another option is to avoid ads by installing an ad blocker extension such as uBlock Origin, a free and open-source browser extension for content filtering, including ad blocking.
Some consumers may also choose to install a privacy browser such as Aloha, Brave, DuckDuckGo or Ghostery on their personal devices. Many privacy browsers have built-in ad blockers; consumers may still see sponsored ads, but they will see fewer of them, which reduces the chances of malvertising.
Consumers who encounter suspicious ads should report them to the relevant search engine for investigation and removal if they are deemed malicious, according to Collis. This can help protect others from being trapped.
Taking proper safety measures is especially important since there are millions of ads on the internet and cybercriminals are persistent. “You should assume that this could happen to you no matter how careful you are,” Madnick stated.
According to Federal Trade Commission data, identity theft of children under age 19 is a growing problem.
Most parents would take significant steps to protect their children. However, many overlook a relatively simple way to help bolster a child’s financial security: freezing the minor’s credit.
This could be particularly important following a major breach in which the Social Security numbers of numerous Americans might be available on the dark web. While locking their credit won’t resolve all cybersecurity issues related to stolen Social Security numbers, it’s an additional layer of protection parents can implement.
The credit-locking process entails contacting each of the three major credit bureaus — Experian, Equifax and TransUnion — and providing necessary documentation including the child’s birth certificate, Social Security card, proof of address and parent identification.
The bureau then generates a credit report for the child and subsequently locks it, preventing loans or credit cards from being issued using the child’s personal information. The freeze remains in place until the parent, or in some cases, the child, requests that it be lifted, temporarily or permanently.
Parents can take these steps proactively even if there’s no indication that a minor’s credit has been compromised, such as unexpected credit card solicitations or bills received in the minor’s name.
It can take some time and effort to lock a child’s credit, but the investment is minimal compared to what can be a lengthy and emotional credit restoration process.
“As an adult, if our credit is stolen, it makes us angry, but we do what needs to be done and we move forward,” said Kim Cole, community engagement manager at Navicore Solutions, a nonprofit credit and housing counseling agency.
But for children, the emotional impact is much greater, she said. “It can take years to get wind of a problem, and meanwhile the damage can continue to grow.”
Identity theft against children — especially very young ones — often goes unnoticed until they are older teens or young adults applying for their first credit card, trying to finance a car or seeking student loans, according to Loretta Roney, president and chief executive of InCharge Debt Solutions, a nonprofit provider of credit counseling and other services.
However, there is a growing problem of identity theft among children under 19 years old. According to data from the Federal Trade Commission, this age group made up 3% of all identity theft reports in the first half of 2024, compared to 2% between 2021 and 2023.
Thieves may use a child’s Social Security number, name, address, or date of birth to apply for government benefits, open bank or credit card accounts, apply for loans, sign up for utility services, or rent a place to live, according to the FTC. While locking a child’s credit won’t protect against all of these, it is a step in the right direction, according to financial professionals.
Not only strangers commit fraud against children. For example, a friend’s uncle destroyed his credit and started using his niece’s name and Social Security number to open credit cards and max them out.
He had the bills sent to his house, and the young woman only discovered the fraud about four years later, when she went to buy a small fixer-upper and realized she had nearly $50,000 of debt in her name and a credit score in the low 500s.
The niece filed a police report, a complaint with the FTC, and disputed the items with the credit bureaus, but it took time to resolve. She applied for a secured credit card since her score was too low to qualify for a traditional card. situation pushed back her home-buying by a few years, ultimately costing her more.
Check if the child has a credit report.
Before locking a child’s credit, it is good practice to check with each of the three major credit bureaus to see if a report exists. Generally, this will only be the case if someone has fraudulently taken out credit in the minor’s name or if the child has been named an authorized user on an adult’s credit card.
To check if their child has a credit report, parents can send a letter with their request to each of the credit bureaus. They should include a copy of the child’s birth certificate, Social Security card or document from the Social Security Administration showing the number, and a copy of the parent’s driver’s license or government-issued identification with the current address.
Legal guardians may have to provide the credit bureaus with documents authenticating their status.
If something suspicious appears on the report, contact the companies where the fraud occurred as well as the three major credit bureaus. Also report the child identity theft to the FTC, with as many details as possible.
If the report comes back clean, the next step is to actually lock the child’s credit.
If necessary, freeze a child’s credit.
The process for initiating a credit freeze varies slightly depending on the credit bureau and the age of the minor child. Be sure to follow the precise instructions for each credit bureau. For Equifax, in addition to required documentation, parents need to fill out a form online and submit it via postal mail; minors who are 16 or 17 may request their own security freeze by phone or by mail.
The websites for Experian and TransUnion provide further details on their respective processes, including document requirements and mailing addresses. It can take a few weeks for the bureaus to process these requests.
Keep good records for unlocking later in life.
Parents need to keep safe the pin number they are provided when locking their child’s credit so it can be temporarily unlocked as needed, such as when the child turns 18 and wants to apply for a credit card, said Bruce McClary, senior vice president of membership and media relations at the nonprofit National Foundation for Credit Counseling.
The unlocking process isn’t necessarily seamless and can take time. Equifax, for instance, asks for these requests in writing, with required documentation for identity verification. After age 18, Equifax allows for managing the security freeze online.
Educate children early on protection of personal information.
Parents should talk to their children about best practices with respect to sharing personal information. For instance, they should caution children to be careful about the kinds of information they provide to websites and apps and to keep their Social Security number close to the vest.
Parents may also want to consider credit or identity threat monitoring services or both. Certain providers may offer basic services for free, but family plans that include adults and children and offer a combination of credit and identity theft protection tend to be fee-based.
These services, which can cost around $24 or more per month, may offer more comprehensive protection, including identity theft insurance and fraud resolution services. Parents should carefully consider the options and associated costs.
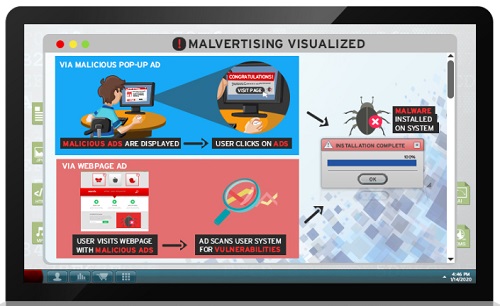
Malvertising, also known as malicious advertising, refers to criminally controlled ads within Internet-connected programs, typically web browsers, that intentionally cause harm by distributing various types of malware, potentially unwanted programs (PUPs), and assorted scams.
In simple terms, malvertising uses seemingly legitimate online advertising to spread malware and other threats without requiring much or any user interaction.
Malvertising can be found on any advertisement on any site, including those visited during everyday Internet browsing. Normally, malvertising installs a small piece of code that directs your computer to criminal command and control (C&C) servers.
The server then scans your computer to determine its location and installed software, and selects the most effective malware to send to you.
“Malvertising can be found on any advertisement on any site, including those visited during everyday Internet browsing.”
How does malvertising function?
Malvertising exploits the same distribution methods used for regular online advertising. Scammers submit infected graphic or text ads (both using JavaScript) to legitimate ad networks, which often cannot differentiate between harmful and trustworthy ads.
Despite the malicious code, malvertising takes on the appearance of common ads like pop-ups (offering fake browser updates, free utilities, antivirus programs, etc.), paid ads, banner ads, and more. Malvertising criminals rely on two primary methods to infect your computer.
The first involves an ad that offers some kind of enticing content to prompt you to click on it. The lure might be in the form of an “alert,” such as a warning that your device is already infected with malware.
Alternatively, it could be a free program offer. These tactics use social engineering to scare or entice you into clicking a link, leading to an infection.
Even more devious is the second method, known as a drive-by download. In this case, the infected ad uses an invisible web page element to carry out its activity. You don’t even need to click on the ad to trigger the malicious behavior.
Simply loading the web page hosting the ad (or a spam email or malicious pop-up window) redirects you to an exploit landing page, which takes advantage of any vulnerabilities in your browser or security loopholes in your software to access your device.
How can malvertising cause harm?
A more relevant way to frame this question might be: is there any chance it won’t harm you? The answer is no, because the criminals behind malvertising have multiple illicit goals that they relentlessly pursue.
They aim to profit by stealing your identification data, financial data, contact data, and more.
Apart from outright data theft, they can encrypt or delete information, manipulate or take control of core computer functions, and spy on your computer activity without your knowledge or consent. This depends on the type of programs the malvertising manages to download. The payloads may include:
Malware, an umbrella term for any harmful program or code.
Ransomware, a type of malware that locks you out of your device and/or encrypts your files, demanding a ransom for their release. Ransomware is a favored weapon of cybercriminals as it demands quick, profitable payments in hard-to-trace cryptocurrency.
The code behind ransomware is readily available through online criminal marketplaces, and defending against it can be challenging.
Spyware, malware that covertly monitors the computer user’s activities without permission and reports it to the software’s author.
Adware, unwanted software designed to display advertisements on your screen, typically within a web browser. It often disguises itself as legitimate or piggybacks on another program to deceive you into installing it on your PC, tablet, or mobile device.
A virus, the original malware that attaches to another program and replicates itself by modifying other computer programs when executed—usually accidentally by the user.
Most cybersecurity professionals agree that viruses are more of a legacy threat than an ongoing risk to Windows or Mac users, as they have been around for decades and have not substantially changed.
Malicious cryptomining, also known as drive-by mining or cryptojacking, is an increasingly common type of malware usually installed by a Trojan. It allows someone else to use your computer to mine cryptocurrency like Bitcoin or Monero.
Instead of allowing you to benefit from your own computer’s resources, the cryptominers send the collected coins to their own account, essentially stealing your resources to make money.
“Criminals who engage in malvertising have various illegal objectives that they vigorously pursue. They aim to profit by stealing your personal, financial, and contact information, among other things.”
Malvertising History
The first known malvertising attack occurred in late 2007 or early 2008, exploiting a vulnerability in Adobe Flash and targeting platforms like MySpace. This incident marked the end of MySpace’s prominence.
In 2009, The New York Times fell victim to malvertising when it published an ad that recruited computers into a larger botnet of malware-infected devices. Readers were presented with deceptive ads informing them of fake system infections, tricking them into installing malicious security software.
In 2010, malvertising spread widely across the internet, with billions of display ads carrying malware across 3,500 sites.
In 2011, Spotify experienced an early instance of a drive-by download malvertising attack.
In 2012, a significant malvertising attack targeted The Los Angeles Times, infecting users via drive-by downloads. This approach became a blueprint for future attacks on large news portals.
In 2013, Yahoo.com faced a major malvertising attack, putting a significant number of its 6.9 billion monthly visitors at risk by infecting their machines with the CryptoWall ransomware.
In 2014, there was a notable increase in malvertising attacks, affecting Google DoubleClick, Zedo ad networks, as well as news portals like Times of Israel and The Jerusalem Post.
In 2015, malvertising attacks continued diversifying, leveraging various popular websites to distribute malicious ads and drop malware onto unsuspecting users’ computers. Targeted websites included dating sites, adult video streaming sites, Google Adwords, and MSN.com.
Malvertising detections have continued to rise. ZDNet reported on a group known as Zirconium, which conducted what was perhaps the largest malvertising campaign in 2017, estimated to have bought one billion ads throughout the year.
Zirconium designed malicious ads with forced redirects to websites hosting fraudulent schemes or malware. It’s believed that this single campaign was present on 62 percent of ad-monetized websites each week.
Malvertising actors have also become more inventive. Cybercriminals are now taking over abandoned domains, displaying malicious ads that force redirect users to tech support scam sites and abusing cryptocurrency miners.
In January 2018, researchers from Malwarebytes found pages with malicious ads containing embedded scripts for Coinhive. While Coinhive has legitimate uses, cybercriminals exploit the service to turn computers into cryptomining machines without users’ knowledge or permission.
What are the primary types of malvertising campaigns?
Once online criminals have obtained information about the user’s computer, software, and location, they use this data to create tailored campaigns. Some campaign categories include:
Schemes promising quick financial gain and other surveys.
These aggressive efforts by unscrupulous advertising networks disrupt browsing with screen hijacks and may offer false lottery opportunities, work-from-home scams, bogus surveys, and other too-good-to-be-true offers. In the past, surveys in this category have even targeted iPhone users.
Tech support scams.
These scams have historically targeted Windows PC users but have also expanded to exploit the assumed sense of security among Mac users. These scams present fake websites as Apple or Microsoft, using JavaScript to prevent victims from naturally closing the page, leading users to call a listed toll-free number for assistance. Scammers, often from India, rely on scare tactics to sell victims hundreds of dollars of worthless “tech support.”
Fake Flash Player (and other software) updates.
This is a common technique to distribute adware and malware to Mac users. These pages masquerade as updates for Flash Player or video codecs, appearing well-designed and pushy. In some cases, the installer will automatically download onto the computer. These campaigns are particularly effective on adult or video streaming websites, as they can entice users to download the application to access desired content. However, users should only download from the product’s official repositories, as look-alikes on infected sites are bundled with potentially harmful software that can slow down a Mac or install spyware.
Scareware
Similar to the tech support scam, scareware initially claims that your Mac or Windows machine is severely damaged or infected, and then prompts you to download a program to resolve the issue. Scareware scams are typically the work of profit-driven malvertising affiliates seeking to generate as many leads as possible to earn substantial commissions from various PUPs.
What types of platforms are susceptible to malvertising?
While Windows has been the primary target of malware attacks for a long time, a malvertising campaign focused on a browser or plug-in can just as easily infect a Mac, Chromebook, Android phone, iPhone, or any similar devices within a business network.
It’s true that cybercriminals primarily target Windows users due to the large user base, which provides malvertisers with the best return on investment. However, Macs are equally vulnerable to malvertising attacks.
In terms of mobile devices, malvertising can pose an even greater threat, as many people do not take the same precautions or have the same level of firewall protection on their phones as they do on their desktop or laptop.
Adding to the risk is the fact that mobile devices are always on and carried from home to work, on weekend outings, and are often used for shopping, making them a prime target for malvertising.
For example, Android users are increasingly affected by malvertising and online fraud through forced redirects and Trojanized apps, which are the two most common examples.
How can I defend against malvertising?
First, address vulnerabilities on your computer and mobile device. Ensure that your operating system, applications, and web browsers (including plug-ins) are kept up to date with the latest security patches.
Uninstall any unnecessary software, especially Flash or Java, as malvertising seeks to exploit weaknesses in such software.
Always practice safe computing and carefully consider before clicking on anything. Be skeptical of any suspiciously alarming notices or scareware, as well as any too-good-to-be-true pop-up offers you receive.
Even if you never click on suspect ads, it won’t fully protect you from drive-by malvertising on reputable sites, but it will reduce your chances of being impacted by much of what the bad guys throw at you, as most malvertising relies on your click to deliver its malware payload.
Enable click-to-play plugins on your web browser. Click-to-play plugins prevent Flash or Java from running unless you specifically allow them to (by clicking on the ad).
A significant portion of malvertising exploits these plugins, so enabling this feature in your browser settings will provide excellent protection.
Consider using ad blockers, which can filter out a lot of the malvertising noise, preventing dynamic scripts from loading dangerous content.
By blocking all advertisements from displaying on websites, you eliminate the risk of viewing and clicking on potentially harmful ads.
Ad blocking also brings additional benefits, such as reducing the number of cookies loaded on your machine, protecting your privacy by preventing tracking, saving bandwidth, loading pages faster, and prolonging battery life on mobile devices.
However, many of the most reputable news sites rely on advertising for revenue, so they request users to disable ad blockers to access content. Malwarebytes has provided insights on this topic.
There is also extensive guidance on using ad blockers on our blog, outlining some completely free methods available to you for a safer internet experience.
For instance, here’s one of our blog posts about ad blockers and anti-tracking browser extensions. We also cover a few common ad blocking utilities and how to best configure those tools for maximum effectiveness.
Statista’s report recorded more than 5.6 billion malware attacks using 678 different types of malware in a single year. Many internet users have become adept at recognizing and being cautious of suspicious activities and phishing attempts.
Cybersecurity is like a game of cat and mouse, with both malicious and ethical hackers constantly trying to outsmart each other.
This has led unethical hackers to hide malware within innocent-looking digital ads, which are a crucial part of the internet economy.
What if clicking on an ad could lead to a malware attack? How can we know if clicking on an ad will harm our devices and systems?
Malvertising is a new form of malware that poses a significant cybersecurity threat because it targets users through legitimate publishing and advertising platforms. The rapid growth of online advertising has contributed to the widespread use of malvertising.
It can reach a wide range of users due to the extensive reach of the channels through which it is distributed. Detecting and protecting against the harmful effects of malvertising is challenging for both users and ad publishers.
Malvertising is a combination of “malicious advertising.” Attackers insert malware into reputable advertising networks used by well-known websites.
These seemingly harmless ‘infected’ ads contain malicious code that spreads the malware. When a user clicks on them, the code redirects the user to a malicious server, establishes a connection with the device, and installs the malware within seconds.
Malvertising is prevalent because major publishers often use automated third-party applications to display ads on their websites, making it difficult to monitor and control, which benefits threat actors. Malvertising does not directly harm the publishing websites, making it harder to detect.
Malvertising not only damages the reputation of advertising platforms and publishers but can also steal sensitive information from users. If the malware is ransomware, the consequences can be even more severe.
Users who use third-party ad blockers to avoid malvertising directly impact the advertising revenue of both publishers and marketers, which is a significant blow to the online advertising industry.
Malvertising and adware are often confused by users. Although technically different, both are harmful. Adware, which tracks users’ web activity, displays unwanted ads, and steals user data, is often embedded in legitimate applications. However, adware does not usually breach users ‘privacy or take control of their systems or encrypt their data.
The codes used for malvertising are deployed on a publisher’s page, while adware is typically deployed directly on an end user’s device. Therefore, malvertising has a much broader impact on users than adware.
How do malware-infected ads come to be?
Before inserting malicious codes into ads, threat actors often gain the trust of the publishing platform by initially placing legitimate ads. They may also use clickbait ads to evoke strong emotions in users and generate a high click-through rate.
When a user clicks on an infected ad, they are directed to a malicious landing page.
The attackers can use the following methods to infect ads:
– When a user clicks on an ad, they are often redirected through several intermediate URLs before reaching the final landing page. Attackers can compromise any of these URLs to execute malicious code on the system.
– HTML5 allows ads to be delivered by combining images and JavaScript, making it easy for attackers to add malicious code within the ad itself.
– Pixels, used for ad tracking purposes, may contain malicious code placed by attackers. Although a legitimate pixel only returns data to servers, attackers can intercept a pixel’s delivery path to send a response containing malicious code to the user’s browser.
– Attackers can exploit the fact that video players do not typically protect against malware. For example, a standard video format called VAST contains pixels from third parties that could contain malicious codes. Videos may also contain malicious URLs. additionally, when attackers insert malicious code into the pre-roll banner, users don’t even have to click on the video for the malware to be downloaded.
– Attackers sometimes compromise legitimate landing pages of products or services by using clickable on-page elements that execute malicious code.
After a user is directed to the desired location by the attacker, the malware is sent through a browser exploit kit. The harmful landing page gathers information from the user’s device and searches for other weaknesses.
Fortunately, this method is now outdated due to the advanced cybersecurity technologies used by most web browsers. However, attackers have started using forced redirects, automatically directing users to a malicious landing page by controlling the browser navigation.
In 2021, REvil, a cybercriminal group known for using ransomware, paid for a prominent position in Google search results to encourage users to click on malicious links.
Angler, a malicious program, automatically redirected users to a website where vulnerabilities in web extensions like Adobe Flash and Oracle Java were exploited.
Malvertising can take various forms based on how it is carried out and delivered to users’ devices:
- Attackers use pop-up ads while users are browsing, tricking them into downloading fake software.
- Through the drive-by-download method, malware is downloaded without the user’s knowledge by exploiting browser vulnerabilities.
- Attackers can inject their code into a publisher page using inline frames (iFrames) in HTML, delivering malware when a user accidentally clicks on the frame.
To protect yourself from malvertising, publishers must thoroughly check their platform for any infected ad placements and employ security solutions to keep malicious codes away. Users should also be vigilant to avoid downloading anything malicious to their devices.
Users can mitigate risks by following these practices:
- Keep your browser and plugins up to date.
- Avoid using Flash and JavaScript.
- Use high-quality ad blockers.
- Have legitimate and updated antivirus software and application security resources.
- Ensure all downloads come from official websites and verified resources.
You might be a victim of malvertising if your device becomes suspiciously slow or if there are unfamiliar apps installed. Follow these steps if you suspect your device has been compromised by malvertising:
- Disconnect from the internet.
- Enter Safe mode.
- Avoid logging into accounts to prevent attackers from obtaining important credentials.
- Delete temporary files that may contain malware.
- Check Activity Monitor (Mac) or Task Manager (Windows) for suspicious programs.
- Run a reliable malware scanner.
- Repair your browser by reinstalling it, removing unwanted plugins, or clearing your cache.
Malvertising is a highly advanced and stealthy form of cybersecurity attack that significantly impacts online advertisers, publishers, and end-users. It is the responsibility of both users and publishers to take necessary steps to mitigate the impact of malvertising.
What is the significance of browser security?
Users often configure web browsers for their convenience, but this can compromise their safety. Using an insecure web browser can make users vulnerable to hackers, data theft, malware, and other risks.
How can I enhance my browser’s security?
There are a few quick measures you can implement to improve your browsing security. Start by blocking browser cookies, disabling saved passwords, installing robust antivirus software, using a VPN, turning off autofill, and keeping your browser updated.
Which antivirus software is the most effective?
Several options are available for top antivirus software. Avira is considered the best value, McAfee offers comprehensive features, and Emsisoft provides advanced defenses.
If you’re not cautious, advertisers, hackers, governments, and companies can track your online activities. What’s the best way to prevent this? One approach is to use a secure browser that helps protect your online identity, enabling you to reclaim your privacy rights.
Leading secure browsers make it easy to safeguard your privacy and security while using the internet.
Most people have a preferred browser for daily use, but does it rank among the top secure browsers? This article will address that question.
Whether you’re browsing the web, conducting business, or connecting with loved ones, chances are you use a browser as your gateway to the internet. Since you share personal and potentially sensitive information, you may also want to use the best identity theft protection available.
If your browser isn’t secure enough, malware could infiltrate your systems, infect your devices, and cause significant harm to your important data.
While antivirus software can make your internet browsing safe and secure, it’s wiser to prevent malware from entering in the first place rather than fixing the damage afterward. By choosing a secure browser, you’ll not only protect all your data but also ensure that no one can snoop on your online activities.
Key Browser Security Features
Regrettably, in today’s world, a simple internet search for the best local restaurants or a quick glance at your bank account can expose internet users to various risks. From marketers mining your data for profit to hackers seeking personal information, it’s no surprise that online privacy is a major concern in the tech industry.
A secure browser with privacy-focused security features is crucial for safeguarding personal data from these malicious activities.
Blocking Third-Party Trackers
Several popular web browsers act more like data collection agencies for advertisers than consumer tools. They track and store users’ browsing history, then sell that data to corporations for advertising purposes, allowing tech companies to monetize your data.
While some users find this helpful as it provides tailored search results, others view it as a privacy breach. If you fall into the latter category, ensure your web browser blocks all third-party trackers and storage to prevent tech companies from collecting and storing your online search data.
Incognito Browsing
Despite the perception that incognito or private browsing is secure, it still exposes you and your data. Although private browsing erases your information, your IP address and location are still shared with every website, ad, and tracker that loads in your browser.
This information can be sold to third parties. Incognito mode also enables people to spy on your computer activities through key-logging software.
Password Management
Storing passwords in browsers for automatic logins to frequently used websites is convenient but leaves you vulnerable to hackers. Browsers typically store these passwords using plaintext.
Use password management software for enhanced password protection. A secure password manager stores user information and passwords in an encrypted archive, ensuring your data isn’t vulnerable to attacks.
Browser Compartmentalization
Most of us use the same browser for email, web surfing, social media, and more while being continuously logged into all our accounts. Services like Gmail and Facebook track your web browsing activities while you are logged in to their websites.
To prevent this, one easy way is to separate your browsers. Use one browser just for web browsing and another solely for online accounts that need a password.
Ensure that you adjust the privacy settings to turn off cookies and prevent the browser from storing your browsing history. Also, remember to always log out of social media and email accounts when not in use.
The Most Secure Browsers of 2024
Brave is possibly one of the top web browsers for overall security. This open source browser comes with a built-in ad blocker, a script blocker, automatic HTTPS upgrades, blocks all third-party storage, and guards against browser fingerprinting.
One of the main benefits of using Brave is that its privacy features are set up automatically. Users don’t need to customize features to enhance their security.
Firefox is a good choice for privacy and security, but users need to customize the settings for optimal security. By default, Firefox collects and stores your usage and performance data. To opt out of this, disable telemetry data collection. Spend time in the privacy settings to enable pop-up blocking, anti-fingerprinting protection, and phishing protection.
Google Chrome is popular due to its functional and enjoyable interface. While the company maintains its security features with regular updates, it’s safe to assume that all your browsing activities on Google are collected, saved to your data profile, and used for targeted advertising. difficult to determine how Google tracks its users as it’s not open source, but it’s not a good option for anyone concerned about privacy issues.
Advanced Security Options
Antivirus Software
Investing in antivirus software is essential to create a secure browsing experience. This software protects your computer from malware and cybercriminals by continuously scanning for malicious attacks. There is a wide range of options available with various price points and security features.
VPN
Virtual private networks (VPNs) help secure your web traffic data against hackers, snoopers, and marketers by allowing you to establish a secure internet connection. VPNs use end-to-end encryption to conceal data and IP addresses by routing data through an encrypted tunnel . This is especially valuable when using public Wi-Fi networks, which are susceptible to hackers.
VPNs are popular for various reasons, but not all VPNs are equally reliable.
Choose one of the most secure browsers and browse the web smoothly
While there are many steps you can take to make internet browsing safe and secure, such as minimizing sensitive information, using strong passwords, and keeping your software up to date, the first step should be selecting one of the most secure browsers.
If you’re comfortable sharing your personal information with Google, Google Chrome offers excellent security and a simple user experience. If you’re concerned about privacy, then Mozilla Firefox is the best choice. And if you’re a tech-savvy individual looking For a secure browser for Linux, Tor Browser is a clear option.
What is a secure browser?
In simple terms, a secure browser is everything a browser should be but enhanced with an additional layer of security to keep its users safe from cybercriminal activity while browsing the internet. It creates a whitelist, which is a list of sites, programs, and online activities classified as secure, and keeps its users safe by blocking all functions not included in this list during startup.
While browser security and privacy are not the same, they ideally go hand-in-hand. While browser security deals with malware and maintains all layers of defense up to date, the privacy aspect primarily focuses on protecting your data and concealing your identity.
Nevertheless, a browser considered strong in security should possess both of these characteristics in similar proportions.
How to choose the most secure browser?
Since there is no shortage of malware, hackers, and identity thieves on the internet, your chosen browser should be able to shield you from all kinds of cyber threats, including phishing sites, web cookies, spyware, keyloggers, and malicious pop-ups.
Additionally, a secure browser that prioritizes privacy will allow its users to delete all browser history whenever they want and safeguard their personal information from others. It should also enable you to use passwords alongside a browser to further protect all your data.
Considering there are several solid and secure browsers across multiple operating systems (OS) and devices, choosing the right one for you can be a challenge. To simplify the search, here are our top picks for the most secure browsers on the market.